Asymmetric cryptography is a process by which a message is encrypted and decrypted simultaneously with a pair of related keys to protect against unauthorized use or access. It ordinarily utilizes both a public and a private key. It is otherwise called public-key cryptography. A public key is a kind of cryptographic key that can be utilized by anybody to scramble a message. Thus, it must be decrypted by the expected beneficiary with their private key. On the other hand, when it comes to a private key it can only be shared with the originator of the key. So at whatever point somebody sends an encoded message, they can likewise do as such by pulling the planned beneficiary’s public key from the public index as well as utilising it to scramble the message prior to sending. It is better to start investing a small amount of money by choosing a reliable platform like the BitSoft360 platform.
Wherein the recipient of the same message can decrypt the message through the use of his/her respective private key. This way the encryption and decoding processes continue naturally; Clients don’t have to physically lock and open any sort of message actually.
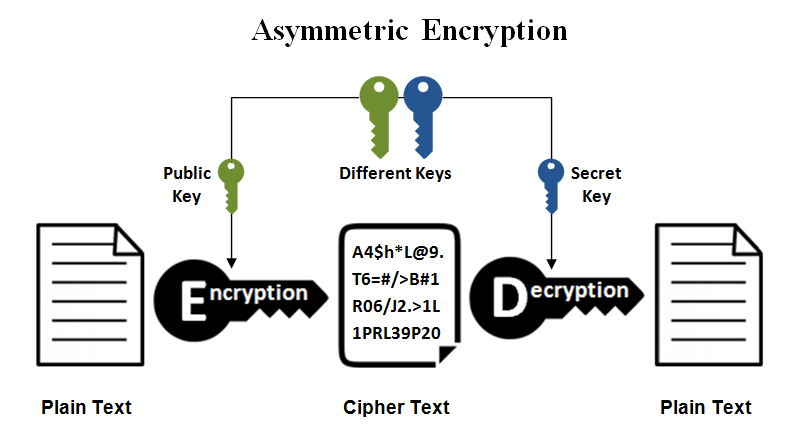
How does asymmetric cryptography work?
Asymmetric encryption typically involves numerically related keys for encryption and decoding: one of which is the public key and one of which is the private key. In which the public key is utilized for encryption and the private key is utilized for unscrambling. The other way around, on the off chance that the private key is utilized for encryption, the public key is utilized for decryption. In the same asymmetric encryption workflow, two types of participants are involved, one is the sender and the other is the recipient. which have their pair of public and private keys.
First, it is observed that the public key of the recipient is obtained by the sender. Next, the sender encrypts the plaintext message through the use of the recipient’s public key. In this way, a ciphertext is produced. The ciphertext is sent to the receiver, which decrypts it with its private key and returns it as a readable plaintext. Although, because of the one-way nature of the encryption capability, one shipper is totally unfit to peruse the other source’s messages, regardless of whether each has the collector’s public key.
Use of asymmetric cryptography
Talking about the main use of asymmetric cryptography is usually done to authenticate data through the use of digital signatures. A digital signature, which is a common mathematical approach, can be used to verify the integrity and validity of a message, digital document and piece of software. It acts as a handwritten or stamped seal’s digital replacement. Digital signatures, which are based on asymmetric cryptography, can confirm the provenance of a transaction or message, provide identification documentation, confirm the status of an electronic document, and acknowledge the signer’s free and informed consent. In addition, asymmetric cryptography applies to systems in which multiple users want to encrypt and decrypt their messages, including:
Encrypted Email. A public key is expected to encrypt a message and a private key is expected to decrypt a similar message.
SSL/TLS. The utilization of asymmetric encryption assumes a significant part in laying out encoded joins among websites and browsers.
Cryptocurrencies. Among cryptocurrencies, there are other cryptos like Bitcoin which have been found to rely on asymmetric cryptography. Users typically have public keys that can be viewed by everyone, as well as private keys that can be kept secret. A cryptographic algorithm is used by BTC to make it easy to ensure that only the legitimate owners are spending the funds. Every unused transaction output (UTXO) on the BTC ledger is moreover often connected to a public key.